SOC 2 Compliance, Certification & More [All the Essentials]
![SOC 2 Compliance, Certification & More [All the Essentials]](https://www.intradyn.com/wp-content/uploads/2022/01/SOC-2-Compliance-Certification-and-More-All-the-Essentials.jpg)
Data has become one of the most sought-after assets in the world, surpassing even oil in terms of value — and Software as a Service (SaaS) companies have access to massive quantities of it. Although this digital goldmine offers numerous benefits, it also presents certain challenges, especially when it comes to customer data.
Every day, customers entrust SaaS companies with sensitive data with the expectation that that data will be securely stored, minimally shared and used in good faith. In order to ensure that customers’ trust is not misplaced — and to prevent costly data breaches and reputational damage — SaaS companies must demonstrate that they’ve made sufficient investments in data security controls, policies, and procedures. Obtaining SOC 2 compliance is just one way of doing that.
What is SOC 2?
Service Organization Control 2 — more commonly known as SOC II or SOC 2 — is an auditing procedure developed by the American Institute of Certified Public Accountants (AICPA) to ensure that companies manage customer data in a secure way.
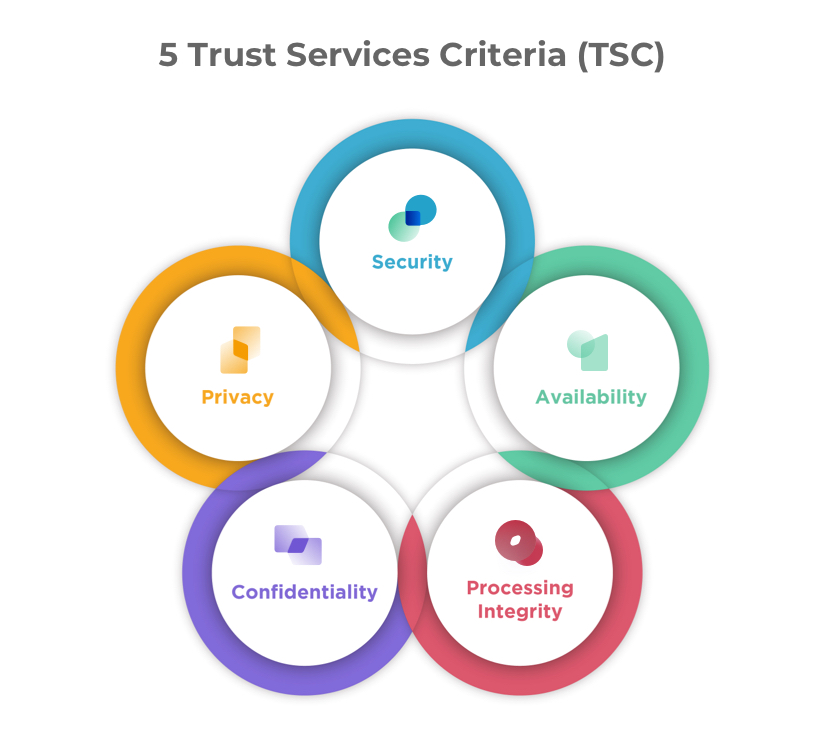
The SOC 2 framework is based on five Trust Services Criteria (TSC), which the AICPA defines as follows:
- Security — Information and systems are protected against unauthorized access, unauthorized disclosure of information, and damage to systems that could compromise the availability, integrity, confidentiality, and privacy of information or systems and affect the entity’s ability to meet its objectives.
- Availability — Information and systems are available for operation and use to meet the entity’s objectives.
- Processing Integrity — System processing is complete, valid, accurate, timely, and authorized to meet the entity’s objectives.
- Confidentiality — Information designated as confidential is protected to meet the entity’s objectives.
- Privacy — Personal information is collected, used, retained, disclosed, and disposed to meet the entity’s objectives.
According to the AICPA, these TSC are used to:
“…evaluate and report on controls over information and systems (a) across an entire entity; (b) at a subsidiary, division, or operating unit level; (c) within a function relevant to the entity’s operational, reporting, or compliance objectives; or (d) for a particular type of information used by the entity.”
SOC 2 is not to be confused with SOC 1 or SOC 3, which are similar, but slightly different. While SOC 2 pertains to internal controls related to data security, confidentiality, privacy and so on, SOC 1 pertains to internal controls related to financial reporting.
SOC 3 is essentially a version of SOC 2 — more specifically, it refers to the audit report a company generates and makes available to the public once it has obtained SOC 2 certification. Although SOC 2-compliant companies are not required to issue a SOC 3 report, many choose to use them as marketing collateral to demonstrate their commitment to data security.
Who Does SOC 2 Apply to?
You might have noticed that the AICPA’s definitions for the five TSC make repeated use of the term “entity.” Simply put, an entity is any company that stores, manages and processes customer data.
An entity becomes a user entity when it retains the services of a service organization — that is, an organization or segment of an organization that stores, manages and processes customer data pursuant to providing a service for an entity. A service organization can be a third-party vendor, a software partner, or a support organization; common examples of service organizations include payroll processors, hosted data centers, cloud service providers and employee benefits plans.
In order to achieve SOC 2 compliance, a company’s internal systems and controls and the systems and controls of any service provider it works with must meet all five TSC.
Why is SOC 2 Compliance Important?
Compared to many other regulations, the SOC 2 auditing process is entirely voluntary. That said, there are many benefits to be gained by achieving SOC 2 compliance. For example, you can:
- Ensure that you have the necessary tools to monitor business operations in real time, anticipate threats and take the appropriate measures to prevent unauthorized access to systems and data.
- Demonstrate to customers that your company has a strong security infrastructure and practices in place, providing much-needed peace of mind and improving your company’s reputation.
- Reduce costs associated with data breaches, including technical investigations, disaster recovery, legal and regulatory activities, loss of business, and reputational damage.
- Access valuable insight into the strength of your company’s security posture, including potential risk, governance policies and more, and proactively identify opportunities for improvement.
- Get a more comprehensive view of security incidents in order to better understand the scope of the situation and engage in more informed and effective remediation.
- Support compliance with other key regulations, including the Health Information Portability and Accountability Act (HIPAA), ISO/IEC 27001 and the Payment Card Industry Data Security Standard (PCI DSS).
- Gain a competitive advantage over companies within your industry that are not SOC 2 compliant.
What Does the SOC 2 Compliance Process Look Like?
In order to obtain SOC 2 certification, a company must undergo a SOC 2 audit performed by a Certified Public Accountant (CPA) or accountancy organization.
According to I.S. Partners, a CPA firm that specializes in performing SOC 2 audits and helping companies achieve SOC 2 compliance, there are two types of SOC 2 audits:
- SOC 2 Type I — “This type of audit examines the controls that service organizations use to address any or all five of the Trust Service Criteria. This audit type describes the service organizations’ systems and provides assurance that controls are effectively designed to meet relevant trust criteria at a specific point in time.”
- SOC 2 Type II — “This audit type includes additional attestation that a service organization’s controls undergo testing for operating effectiveness over a period of time. User organizations and their auditing team generally select six months for the period of time to evaluate.”
Most companies prefer to undergo a SOC 2 Type II audit, as it is more comprehensive and therefore more reliable than a SOC 2 Type I audit.
During the audit process, an auditor will evaluate the effectiveness of controls within your entity’s — or your service organizations’ — cybersecurity risk management program according to the AICPA’s five TSC. The process itself can include anything from employee interviews and systems testing to records requests and filling out paperwork. Generally speaking, auditors are looking for the following controls and policies:
- Access controls
- Disaster recovery
- Encryption
- Intrusion detection
- Network and application firewalls
- Performance monitoring
- Processing monitoring
- Quality assurance
- Security incident handling
- Two-factor authentication
Once the audit is complete, they will generate a detailed attestation report based on their findings. These reports typically include:
- Details on the scope and purpose of the audit;
- Notes on adherence to each of the five trust service criteria;
- Test procedure and testing results;
- A letter of opinion;
- Management assertion, and;
- The auditor’s final determination.
If your company successfully passes the audit, you can share the results of your SOC 2 report with your customers as a demonstration of your company’s strong security controls and standards.
What Are Some Best Practices for Obtaining SOC 2 Certification?
If your company is scheduled to undergo an SOC 2 Type I or Type II audit, there are a few measures you can take to ensure you’re adequately prepared:
- Determine which trust principles you intend to have audited. All SOC 2 audits cover data security, but you can also choose to audit your company’s data availability, processing integrity, confidentiality and privacy. You also have the opportunity to define the specific controls you wish to audit.
- Conduct a readiness assessment. A readiness assessment will help you identify any potential gaps within your existing security processes and controls that might leave you at risk of failing your audit. Once you have a clear sense of which areas are in need of improvement, work with your company’s internal cybersecurity team or partner with a third-party cybersecurity professional to make the necessary changes.
- Establish a baseline for normal activity within your cloud environment. This allows for continuous security monitoring and makes it easier to restrict user access as needed, detect unauthorized — and potentially malicious — activity, and create a centralized record of any system or configuration changes.
- Set up anomaly alerts. Your company’s security incident alerting procedure will be subject to review in your SOC 2 compliance audit, so it’s important to ensure that you have alerts in place — and that your procedure is designed to eliminate the potential for false alerts.
- Create detailed audit trails. If your company does experience a security incident, be sure to apply actionable forensics in order to fully identify the root cause of the attack, its source of origin, the total scope of the event, the context in which it took place, and any other pertinent details. Once you’ve surfaced this information, carefully record it. By creating detailed documentation around security incidents, you can gain valuable insights into potential vulnerabilities in your security posture and develop more robust remediation plans.
- Choose your service organizations carefully. Even if your own company takes all the necessary precautions to safeguard customer data, vulnerabilities within your service organizations’ systems can put you at risk of failing to achieve SOC 2 compliance. Bearing that in mind, partner only with third-party providers who have made sufficient investments in cybersecurity.
At Intradyn, we know just how important data security is, which is why all of our archiving solutions enable organizations to create custom access controls, set role-based permissions, generate detailed audit trails, and backup communications for disaster recovery. We also utilize the latest security measures, including two-factor authentication and AES 256-bit encryption, to ensure that your customers’ sensitive data is kept under lock and key.
To learn more about Intradyn’s advanced archiving solutions contact us today.