What Is Vishing? Prevention, Tips & Examples

You’re likely familiar with phishing scams, but have you heard about vishing? It’s a similar, though slightly different, way for hackers to infiltrate and steal personal information, but this technique uses a phone as opposed to email.
Unfortunately, vishing is becoming all-too-common — 33% of individuals in the United States have fallen victim to a phone scam and 7 out of 10 people have encountered a vishing attack. And all of this comes with a hefty price tag: vishing scams cost Americans a staggering $68.4 million in 2022.
In this guide, we’ll explore the ins and outs of vishing, including the common techniques hackers use and how businesses and organizations can protect themselves against future attacks.
What Is Vishing?
Vishing, which is short for “voice phishing,” occurs when a person fraudulently uses phone or voicemail to obtain someone’s personal information.
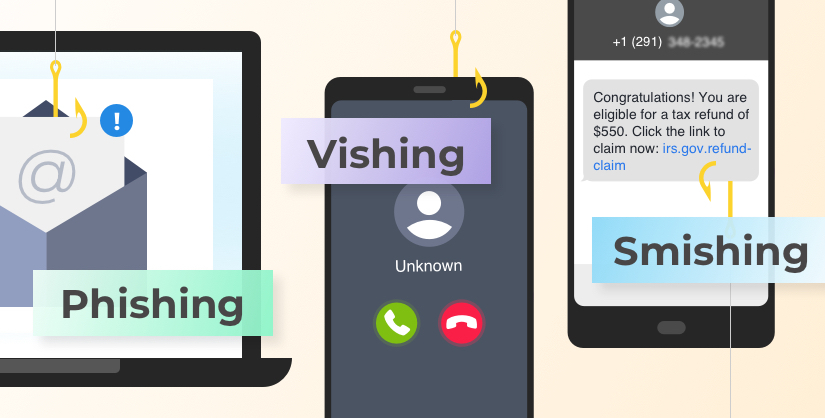
Vishing vs. Phishing vs. Smishing
All three crimes deal with hackers stealing personal information, but the techniques in which they are carried out differ.
- Phishing — This occurs when a hacker uses fraudulent email tactics to obtain personal information such as passwords, bank account information, social security numbers, etc. In many cases, the email contains a link or attachment that tricks the reader into downloading malware.
- Vishing — Vishing is the same concept, but instead of email or electronic communications, the scammer uses either a phone call or voicemail to try and obtain personal information.
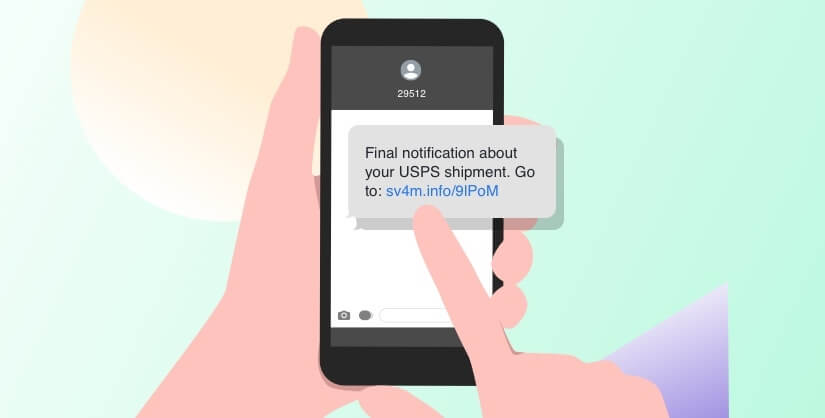
- Smishing — Short for SMS phishing, this is when a hacker uses text messaging and poses as a legitimate business, person or organization with the intent of stealing private data. Similar to phishing, these types of text messages often contain a malicious link.
[RELATED] Put your phishing training to the test. Take the quiz! >>
How Does Vishing Occur?
Each incident may differ slightly, but these are the typical steps of a vishing scam:
- The cyber criminal will often start by researching the potential victim, looking for any bits of personal information that could be used in the scam. This is also referred to as social engineering and is a good reason why it’s important to refrain from posting private information on public social media platforms.
- Scammers will then often use something called neighbor (or caller ID) spoofing, which is when a call appears to be coming from a local number or trusted source.
- Once the scammer has someone on the phone, they will typically “appeal to the victim’s instincts of trust, fear, greed, and desire to help.” In other words, they will play heavily on the victim’s emotions. After the scammer has gained the victim’s trust, he or she may then ask for personal details such as a social security number or banking information.
- If the victim complies, the scammer will then use that important personal information in the future to commit additional crimes.
Common Vishing Techniques
What does a vishing technique actually look like? Here are some common scenarios:
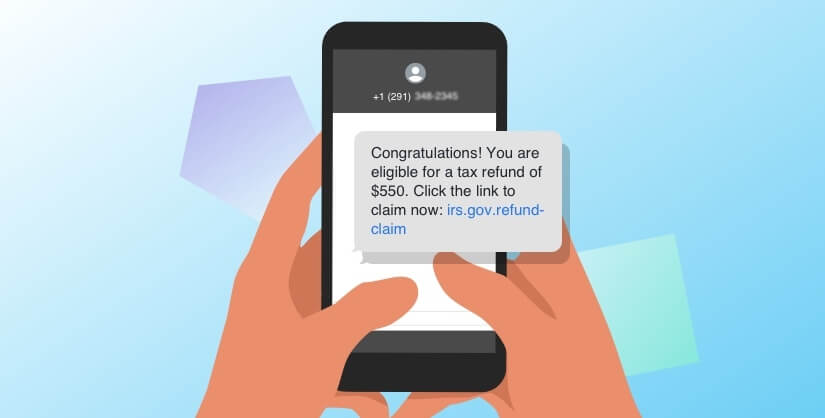
- There’s an issue with your account, and the caller is pretending to be from your bank (or a different organization such as the utility company). The caller may also pretend to work for law enforcement or a particular government agency, such as the IRS.
- You are the recipient of a special award or offer and must submit your personal information in order to claim your prize.
- Other common techniques include enrollment scams, voice cloning and posing as fraudulent tech support.
10 Vishing Examples
Now let’s explore some real-life vishing examples:
- Artificial intelligence (AI) cloning, or deep voice technology, has become an increasingly popular impersonation tool for hackers. In one case, criminals used AI cloning to defraud a Japanese company of $35 million.
- Another popular example that may also use AI cloning is the “grandparent scam” in which hackers use someone’s personal information to impersonate a grandchild or another close relative asking for money.
- In South Korea, the “Letscall” scheme tricked victims into downloading malicious apps from a counterfeit Google Play Store site.
- The Federal Trade Commission recently issued a warning about scammers who are pretending to be law enforcement personnel and threatening to arrest medical professionals for missing a court date.
- Scammers are also impersonating food delivery services. Other vishing examples include charity schemes, scams involving extended car warranties, loan scams, lottery scams and “free” trials.
How to Report Vishing
If you believe you were a victim of a vishing scheme or suspected attack, it’s important to contact your local authorities. You should also report the scam to the government and file a complaint with the FBI’s Internet Crime Complaint Center (IC3). These agencies may also provide additional guidance.
If the hacker is impersonating an employee from a legitimate business, for example, you may want to reach out to the real company and inform them of the situation.
Finally, if your company has been targeted by scammers, you should advise your employees of the incident so that everyone can be on high alert.
How to Stay Safe & Prevent Vishing
Hackers are always evolving their methods, but there are certain steps you can take to prevent vishing attacks.
- If you receive a phone call from a person who is requesting your personal information, hang up. You can then call the business or organization back to determine the legitimacy of the call.
- Report any financial fraud attempts to your bank. Remember to document what was said and what information was requested.
- Be wary of caller ID. Know that many scammers use caller ID spoofing so that you may think the communication is coming from a trusted local source and are therefore more likely to answer.
- An important tip to remember: No one from a federal agency will contact you (or your business or organization) by email, text message or social media to request personal information.
- Join the National Do Not Call Registry, keep important information safe and maintain strong passwords.
If you’re looking for ways to strengthen your business or organization against potential threats, we invite you to contact the team at Intradyn. We have extensive experience implementing archiving software and helping businesses and organizations of all sizes safeguard their private data and information. We also recommend checking out our free data retention policy template as a way to enhance your data retention strategy and policy plan.