What Is Smishing? Prevention, Tips & Examples

Most of us are familiar with phishing, the practice of sending fraudulent emails in order to entice the recipient into giving up personal information, sending money or otherwise compromising themselves. If revealed, information such as social security numbers and PINs can be used to withdraw money from your bank account or steal your identity altogether.
While the email vector of attack is familiar to most, there is a growing threat in the form of smishing, a phishing attack that occurs over text messages (SMS). Worldwide, 1.1 billion spam texts are sent every minute, and that number is only projected to increase. Luckily there are some things you can do to identify and avoid smishing scams before you’re compromised.
In this blog post, we’ll discuss smishing in greater depth before providing smishing examples and finishing up with smishing prevention tips.
What Is Smishing?
Unlike viruses and many other technology-borne threats, smishing is a social engineering attack, relying on tricking the target into revealing their information rather than getting it out of the system through purely technical means.
Smishing exploits people’s trusting nature to gain access to their sensitive information. Often posing as legitimate organizations, texts will claim to need some piece of sensitive information for verification purposes before they can help you manage whatever fictional situation they’ve conjured. While many will recognize these for what they are, the heightened emotion of recipients and sheer volume sent out ensures that at least some people will compromise themselves or their organization.
Most often these texts contain links leading to malicious websites requesting sensitive information or malware that downloads itself onto your phone.
Smishing Examples
Now that you have a better understanding of smishing in general, let’s look at some common types of smishing attacks most people will eventually encounter.
Financial Texts
If you receive a text purporting to be from your bank that your account will be suspended if you don’t provide some piece of verification information, think before responding. While it can be stressful to envision the flow of your finances being interrupted, this is exactly what the scammers are counting on. Remember that all reputable financial organizations always ask you to sign into your account before displaying or requesting sensitive information.
Password Reset Requests
Two-factor identification is a well-known security tool that helps keep accounts safe by requiring verification from multiple devices before allowing a user to log in. Hackers are now mimicking password reset texts, but instead of actually resetting the password, users who click through the links and provide the asked-for information actually give control of the account to the hackers.
CEO Fraud
Preying on people’s desire to impress their superiors, these texts purport to be from someone very high up in an organization, needing something done immediately. While no one takes questioning their CEO lightly, it’s important to remember that CEOs and other executives will always go through proper channels when contacting those within the organization and any malicious texts you receive should be reported to your IT and/or HR department immediately.
Unusual Account Activity
This type of message will claim that there has been unusual activity detected on your account and some piece of information is required to help secure the potential breach. Ironically enough, by providing the requested information, you would, in fact, be causing the breach you were trying to avoid.
Order Messages
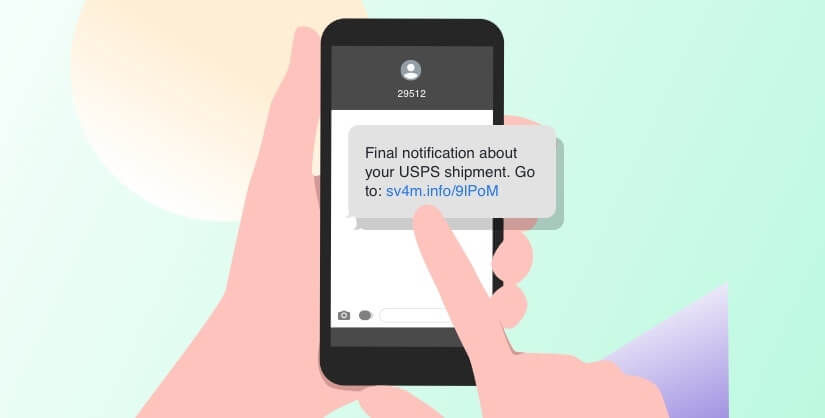
These refer to smishing messages claiming to be about an order being shipped or delivered. As is typical with smishing in general, there’s usually just one more piece of information they need to ensure you receive your package. As most of us regularly have packages delivered, this might seem legitimate on its face; however, you should always make sure that the links lead to the actual company’s website before giving away any sensitive information.
Contests & Giveaways
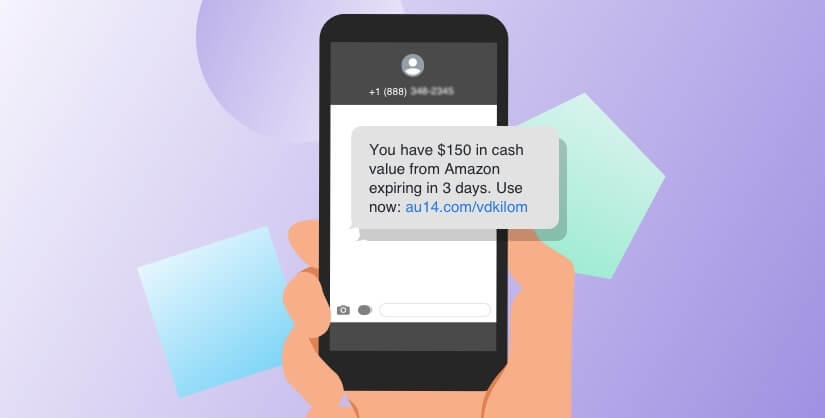
Most of us would be ecstatic to learn we’d just won some fabulous prize in a contest we couldn’t even remember entering. But if that scenario seems too good to be true, it’s probably because it is. Hackers will regularly send out messages with that very content to their intended targets. If you get a message like that, remember, while it would be amazing if true, it’s probably a scam.
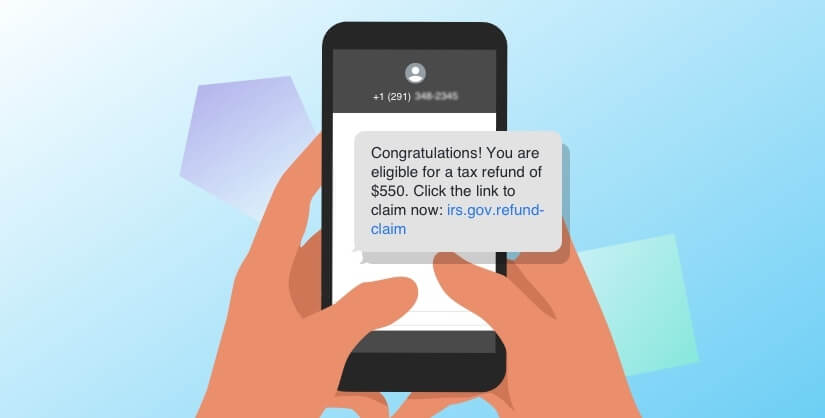
Payment Information Emails
With payment information emails, the target receives an email related to a payment, a refund, an invoice or some other financial transaction from a seemingly legitimate source, such as their bank or credit union. The recipient is then directed to follow a link within the email to collect their payment or pay the invoice, which will bring them to a website where they’re asked to provide sensitive information. To avoid this type of smishing attack, be sure to give your financial institution a call if you receive any unexpected emails regarding a transaction.
Smishing Prevention
The only effective way to stop a smishing attack is to identify and report malicious messages. If the intended victim doesn’t follow a provided link or otherwise take action, then they won’t compromise their information.
Here are some tips for smishing prevention:
- While it can be tempting, avoid taking any action on messages claiming to be offering a prize if you enter identifying information.
- Texts claiming to be from financial institutions asking for confidential information are always scams. Real financial institutions will always direct you to a secure portal before any information is disclosed or requested.
- If you don’t recognize the number, be on higher alert.
- Messages from email addresses, represented by only a few numbers, are often scams.
- Report attacks to your telecom to help protect others from future attacks.
- As a general rule, you should never send sensitive information over SMS.
- Enable spam protection on your mobile devices.
- Keep your phone number secure by limiting who has it.
Smishing is a very real threat to data security and the number of attacks is growing by the day. The good news is that once you learn to recognize these messages for what they are, you have the power to stop them in their tracks. By not taking any actions in response to these SMS messages, you are fully protected from their effects.
Should a breach occur, having a secure and accurate record of how it happened as well as strong backups of compromised information are critical to mitigating damage. Intradyn offers secure email and SMS archiving solutions that will help when determining where and how the breach occurred.
Our Data Retention Policy Template is a great place to start when putting together a comprehensive data retention policy and if you have any questions, please feel free to reach out and someone will get back to you as soon as possible.