What Is IT Risk Management? [+ Best Practices]
![What Is IT Risk Management? [+ Best Practices]](https://www.intradyn.com/wp-content/uploads/2022/09/What-Is-IT-Risk-Management.jpg)
As your organization grows and evolves, so will your information technology (IT) infrastructure, with new systems being added and scaled as needed. These systems — many of which likely house sensitive customer and company data — are subject to risk in the form of cyberattacks, data breaches and even unexpected downtime, all of which could leave your organization vulnerable.
Developing a strong IT risk management strategy can help mitigate risk, improve your security posture and enable your organization to bounce back faster in the event that something goes wrong. In this article, we’ll discuss common risks to IT environments, how to conduct your own risk assessment, how to develop an IT risk management strategy and more.
What Are the Leading Risks to IT Environments?
In the world of IT, the term “risk” refers to anything that threatens the confidentiality, integrity or availability of data assets. Risk can take many forms, including software failure, human error, a natural disaster or more sophisticated cyberattacks, such as:
- Phishing: Phishing is a form of cybercrime in which the attacker poses as a legitimate institution or trustworthy entity in an attempt to secure sensitive information from their intended target. Phishing attacks are a leading threat to information security; according to Verizon’s annual Data Breach Investigations Report, phishing remains one of the most common threat actions.
- Insider threats: An insider threat occurs when someone within your organization shares confidential information — either intentionally or unintentionally — with unauthorized individuals. The Ponemon Institute reports that, on average, impacted organizations spent $15.4 million annually on overall insider threat remediation and took an average of 85 days to contain each incident.
- Malware: Malware collectively refers to any software designed for the purpose of intentionally disrupting IT systems, exposing private information, depriving authorized users of access or providing unauthorized users access. Some of the most common examples of malware include:
- Viruses, which attach themselves to legitimate programs in order to infiltrate a computer and alter its code. Once a virus has altered a computer’s code, it replicates itself and spreads from the host to other systems, hence the reference to biological viruses.
- Trojan viruses, which present themselves as a legitimate program, file or code, but contain a virus hidden within. Trojans derive their name from the ancient Greek story about the Trojan horse and the fall of Troy.
- Worms, which are a type of Trojan virus that self-replicate and spread to other computers over network connections, while remaining active on their original infected systems.
- Ransomware, which encrypts files on a device or within a system, rendering them unusable. Criminals then hold that information hostage, only agreeing to decrypt those files once their victim has agreed to pay a ransom.
- Spyware, which infiltrates a system and runs in the background, collecting information and sending it to an unauthorized third party. Criminals will then either use this stolen data against their intended victim, or sell it to the highest bidder.
- Adware, which displays unwanted advertisements on your computer. Although adware is not as active a threat as some of the other malware listed here, certain adware programs also contain spyware, so it’s important to eradicate them as quickly as possible.
- DDoS attacks: A Distributed Denial-of-Service (DDoS) attacks — sometimes known as distributed network attacks — are designed to interrupt services by flooding servers with internet traffic, thereby preventing users from accessing IT systems, devices and other resources.
- Botnets: A botnet is an entire network of infected computers linked together and used to steal data, send spam and grant unauthorized users access to private information. Botnets are often used to execute DDoS attacks.
- Advanced persistent threat attacks: Advanced persistent threat (APT) attacks are prolonged attacks that use advanced hacking techniques to gain access to a system. Hackers then remain undetected for an extended period of time, stealing data from their target. Given the sophistication and level of coordination APT attacks require, they’re often carried out by organized crime groups, including nation- and state-sponsored groups.
What Is IT Risk Management?
Given the many and varied risks IT systems face, it’s important for your organization to have a strong, well-designed IT risk management strategy in place. IT risk management, or information risk management, simply refers to the complete policies, processes, procedures, protocols, controls and technology that an organization uses to safeguard its IT infrastructure.
An IT risk management strategy typically consists of three key components:
- An IT risk management assessment and analysis, which enables an organization to identify vulnerabilities within its existing environment and determine next steps to close those gaps
- Risk evaluation and prioritization, which involves determining how great of a threat each vulnerability poses to your IT environment and, based on that information, the order in which they need to be addressed
- Risk mitigation, which describes the strategy your organization executes and actions you take to eliminate vulnerabilities and strengthen your security posture
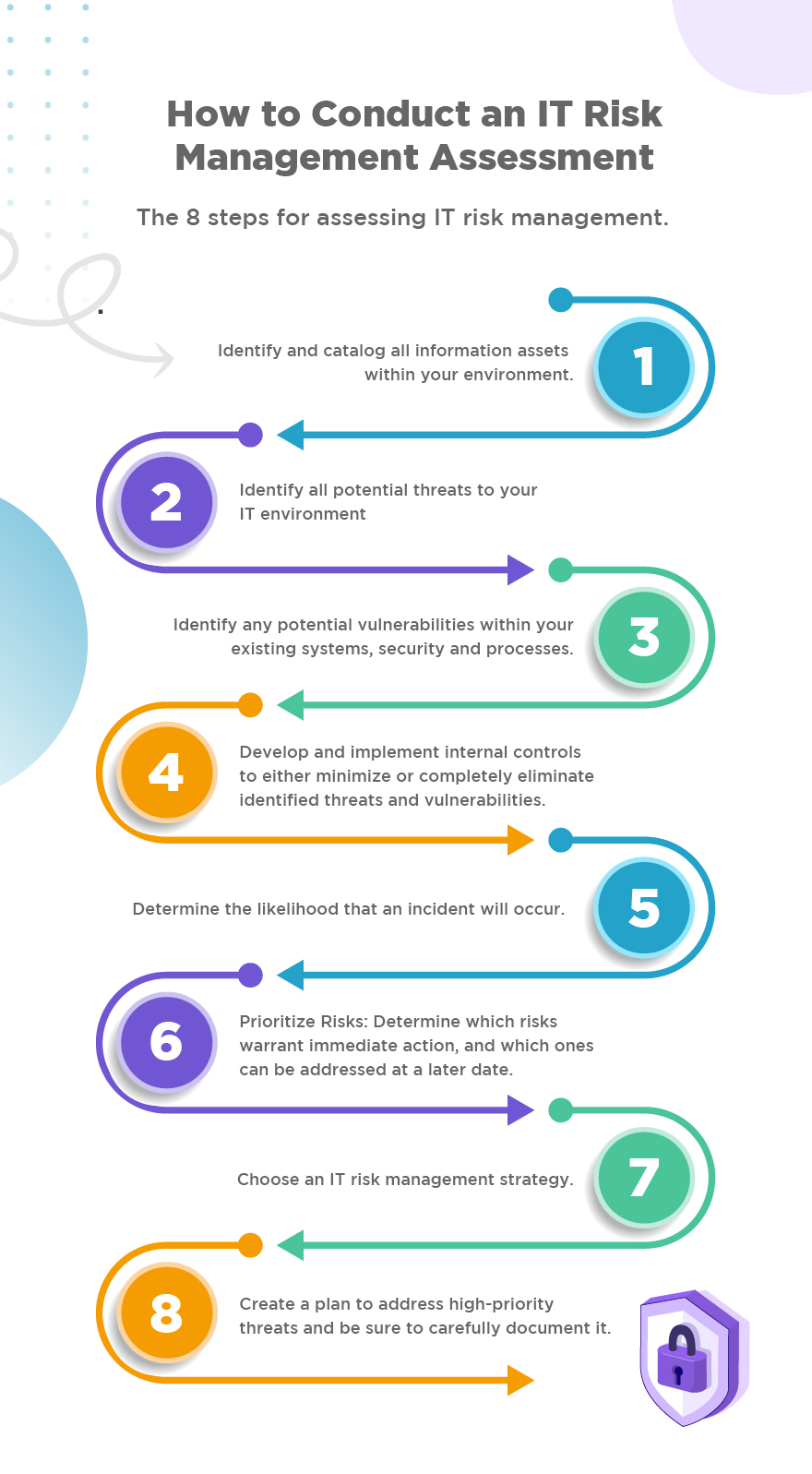
How to Conduct an IT Risk Management Assessment
A risk assessment is perhaps the most fundamental component of any IT risk management strategy — after all, without conducting a risk assessment, you can’t get an accurate picture of what vulnerabilities exist within your IT environment.
Most IT risk management assessments follow the same general process:
- Identify and catalog all information assets within your environment — including servers, data, documents and more — as well as any processes or policies associated with those assets. When cataloging assets, be sure to classify them in terms of their sensitivity; the most common classifications are public, internal-only, confidential and restricted.
This is also a good opportunity to identify key stakeholders within your organization — sales, marketing, finance, legal, HR and so on — who will be integral to upholding and enforcing your IT risk management strategy.
- Identify all potential threats to your IT environment; these not only include cybersecurity threats, such as hackers and malware, but also more run-of-the-mill issues, such as equipment failure, power outages, natural disasters and simple human error. Be mindful to include any unique, industry-specific threats your organization might face, such as regulatory non-compliance.
- Identify any potential vulnerabilities within your existing systems, security and processes. For reference, a “vulnerability” refers to any error or weakness that could be exploited, such as weak passwords, missing or broken authentication, misconfigured system components and SQL injection.
- Develop and implement internal controls to either minimize or completely eliminate identified threats and vulnerabilities. A risk assessment is, in and of itself, a type of internal control; other examples include:
- A control environment, which refers to your organization’s cultural approach to managing risk
- Control activities, which consist of any action your organization takes to carry out your IT risk management strategy
- Information and communication, which refers to data collection, reporting and communications between different teams and departments in service of IT risk management
- Monitoring, which involves conducting routine tests to ensure that your IT risk management processes and policies work as intended
- Using the information you’ve gathered up to this point, determine the likelihood that an incident will occur. To put things simply, the higher the number of potential threats and the more vulnerabilities within your existing environment, the greater your risk. You’ll also want to conduct an impact analysis to gauge the potential fallout of a disruption to your organization.
- Determine which risks warrant immediate action, and which ones can be addressed at a later date. This may seem counterintuitive — after all, all risks pose a threat to your organization — but it’s important to prioritize those that are the most likely to happen and that will have the greatest impact. Once you’re figured out how to eliminate those risks, you can focus your attention on lower-level risks.
- Choose an IT risk management strategy. The most common are as follows:
- Risk Avoidance: As its name implies, the primary goal of this IT risk management strategy is to eliminate all probability of risk taking place. The most common example of risk avoidance in IT is choosing not to collect certain types of data.
- Risk Mitigation: Also known as risk reduction, this strategy involves minimizing your risk exposure as much as possible by using security platforms and network monitoring, investing in backup solutions, restricting systems access to authorized users, defining usage policies, deprovisioning accounts that are no longer in use and so on.
- Risk Transfer: Organizations that utilize this IT risk management strategy will invest in additional resources — such as cyber insurance and offsite, external data storage — to reduce their risk.
- Risk Acceptance: To some extent, risk is unavoidable. Risk acceptance is all about determining what amount of risk your organization can afford to live with.
It’s important to note that your organization isn’t locked into just one approach; in fact, many companies choose to combine elements of each of these techniques when developing their IT risk management strategy.
- Create a plan to address high-priority threats and be sure to carefully document it. You’ll want to include key stakeholders, senior management and members of your IT team when defining physical, technical and organizational controls. You’ll also want to make documentation of controls, policies and procedures easily accessible to users at all levels, so they fully understand what’s expected of them and how they can help secure your IT environment.
IT Risk Management Best Practices
In addition to conducting a risk assessment, there are other measures you can take to protect your IT environment against risk, including:
- Establishing a baseline for normal behavior in your IT environment and then continuously monitoring against that baseline
- Keeping close tabs on industry-specific data regulations, such as HIPAA and FERPA, and general data protection regulations, such as GDPR
- Staying up to date on the latest industry and IT news to keep a close watch on emerging risks
- Investing in a scalable risk management platform capable of growing with your organization
- Investing in a backup solution to reduce the risk of data loss in the event that an incident should occur
- Cultivating a risk-aware company culture by educating employees about potential risks, sharing all IT risk management strategy documentation, clearly communicating expectations and securing buy-in at all levels of your organization
- Conducting a risk assessment not just once, but on a regular, recurring basis and updating your IT risk management policies and procedures based on new findings
- Defining data retention policies that prevent you from holding onto data assets for longer than is absolutely necessary
Frequently Asked Questions
Q: What are the most common IT risks?
A: Risk can take many forms; although cyberattacks such as malware and data breaches are the most common threat, equipment failure, power outages, natural disasters and even simple human error can also pose a threat to your IT environment.
Q: Why is it important to have an IT risk management strategy in place?
A: An IT risk management strategy boasts numerous benefits, including protecting your systems from data breaches, reducing the risk of unexpected downtime, ensuring business continuity and providing customers (or whomever you serve) with the peace of mind of knowing that their personal information is safe.
Q: Who is responsible for IT risk management in an organization?
A: In most organizations, the IT department is in charge of IT risk management. However, a truly successful IT risk management strategy requires the buy-in of key stakeholders across all teams and departments and the adherence of users at all levels of the organization.
Q: How does a risk assessment support a strong IT risk management strategy?
A: Conducting a risk assessment can help your organization establish a baseline for normal activity within your IT environment, identify potential threats to and vulnerabilities within your infrastructure, prioritize threats according to their severity, develop strong protocols and controls and more. In short, a risk assessment provides the foundation for any successful IT management strategy.
Q: How often should my organization conduct risk assessments?
A: The general rule of thumb is that you should conduct a risk assessment once per year.
Q: Are there any software solutions that can help prevent information risk?
A: There are a wide variety of tools and software you can invest in to help improve your organization’s IT security posture, including cybersecurity systems, risk management platforms and backup solutions.